Mastering Cloud Permission Security
Here's a rewritten version that sounds more natural and less AI-generated:
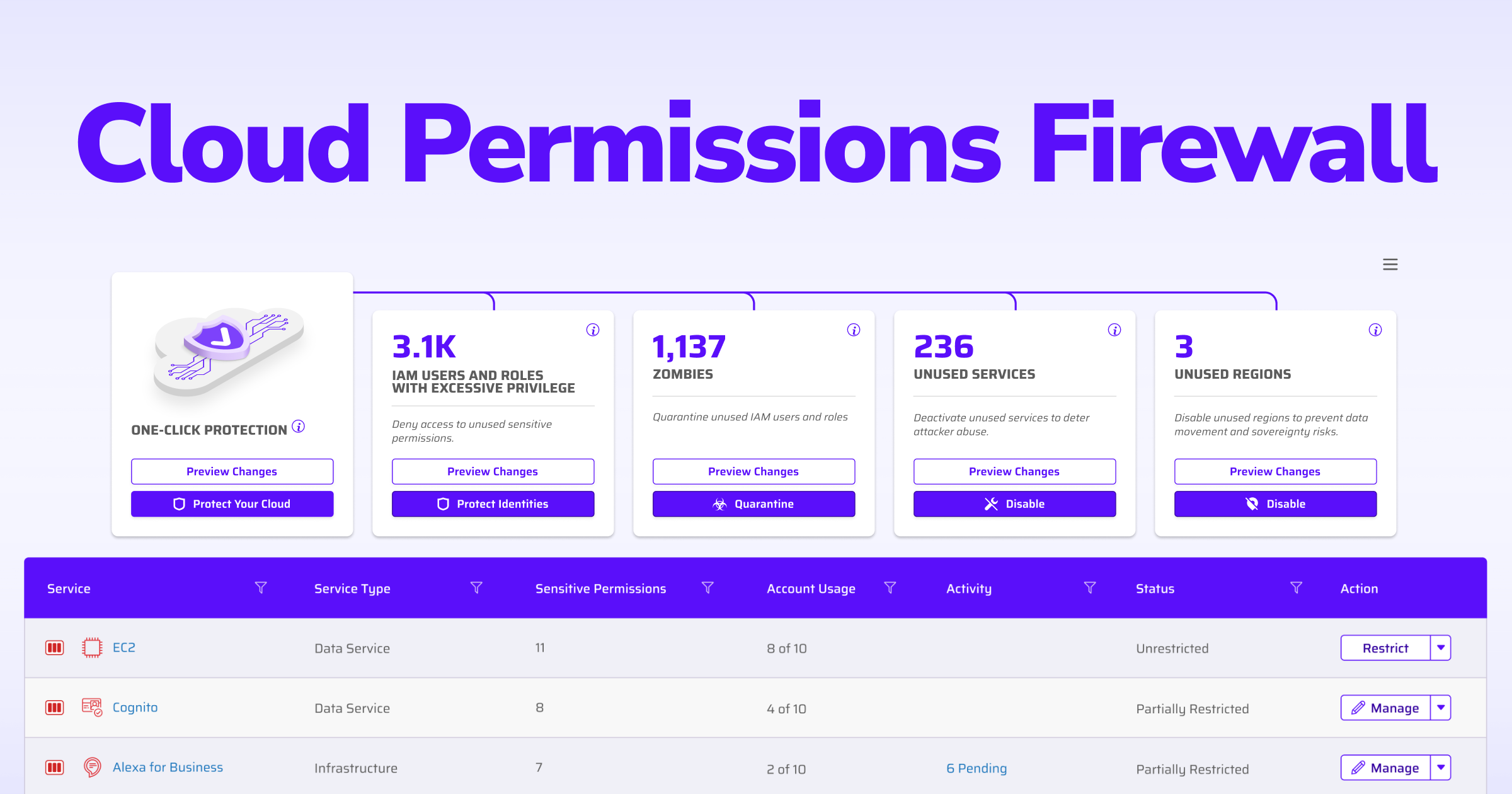
Poorly managed cloud permissions can have serious consequences, exposing sensitive data and critical systems to unauthorized access and other security risks. When permissions aren't properly configured, it can lead to "cloud zombies" - abandoned user accounts and resources that expand an organization's vulnerability. Overly broad privileges given to users and services can also enable attackers to gain elevated access through privilege escalation.
Tackling these cloud security issues requires a comprehensive strategy that combines technical measures, organizational processes, and a security-focused culture.
Dealing with Abandoned Accounts
As organizations rapidly adopt cloud services for agility and scalability, they often neglect to properly remove outdated user accounts and resources. This oversight can result in a mess of inactive accounts with no clear ownership, potentially retaining excessive permissions that could be exploited by attackers.
To address this, organizations should:
• Create a complete inventory of all identities and their permissions across cloud environments
• Regularly review and clean up unused accounts and permissions
• Establish formal processes for managing cloud identities throughout their lifecycle
• Use tools to automatically flag and isolate suspicious or inactive accounts
• Educate users on proper account management and associated risks
Implementing Least Privilege Access
Many organizations grant excessive cloud permissions, often due to rushed "lift and shift" migrations that prioritize speed over security. While the principle of least privilege - giving users only the minimum permissions needed - is a security fundamental, it's frequently overlooked in cloud environments.
Automating Access Control
Manual permission management becomes impractical as cloud usage grows. To address this, organizations are turning to automated solutions that manage permissions while ensuring proper governance. These "permissions on demand" approaches use technology, processes, and policies to grant minimal necessary permissions and properly review any changes.
A key feature is the ability to quarantine unused or suspicious cloud identities and resources. When these attempt to use elevated permissions, the system can automatically block the request and notify the appropriate team for review. If approved, permissions are granted and the quarantine lifted. If denied, the quarantine remains in place for further investigation.
Tools like Sonrai Security's Cloud Permissions Firewall can help implement this model, integrating with existing cloud infrastructure and identity systems to streamline permissions' management.